Abishek Muthian
Major disaster has struck the computing industry.
TL;DR your computers are going to get slow because of patches aimed at fixing unprecedented vulnerabilities in the CPU.
For the rest (simplified),
Modern computational security relies on maintaining the sanctum of memory, i.e keeping secure memory (say your passwords) out of access from user process (the meme website). The guard duty for this falls on CPU’s working in tandem with the OS.
Recent security vulnerabilities in the CPU (>1995) has been disclosed which allows an attacker to breach this sanctum and steal data. OS manufacturers are releasing an update to patch this by not actually fixing it as it requires CPU to be redesigned, but by isolating secure memory; this means accessing secure memory is going to get expensive and thereby slowing down the computation.
If your are interested in reading the technicality of the vulnerabilities, feel free to click on the Project Zero link.
The vulnerabilities disclosed are being called Meltdown & Spectre, one allows access to secure memory & other allows data to be stolen.
I’ve been avoiding buying expensive CPU’s for nearly a decade now, conducting my general computation tasks mostly on in-expensive SOC’s and demanding tasks over cloud with beefier CPU’s. I strongly believe, if not a gamer the law of diminishing returns affects CPU extensively for a consumer as all-most every day-to-day tasks can be conducted over a cheaper computer, smartphone or tablet. This is one of such times I’m glad of such decision.
Yet with ball-park performance impact of 30%, it’s going to get expensive for businesses who rely on cloud computing; but let's wait till the patches arrive and benchmarks tell the real story. The priority is and always must be security.
Update
Benchmarks are in after KPTI patches ,
Our Node.js, MongoDB, Python servers at Timebender Technologies all with significant network traffic didn’t have any measurable impact after KPTI patches on Amazon Linux on T2.medium(burst), M4.large, T2.large(burst) respectively.
Our impact is lesser than the figures suggested by redhat’s advisory — https://access.redhat.com/articles/3307751
Phoronix has been conducting wide variety of benchmarks on the impact of KPTI patches and concluded similarly.
Unless you run work load uses heavy cached random memory with buffered IO, you shouldn’t have to worry about the performance impact and I would suggest you to update to latest security patches.
Perhaps, epic games run one of such aforementioned work loads; they have witnessed huge impact on performance —
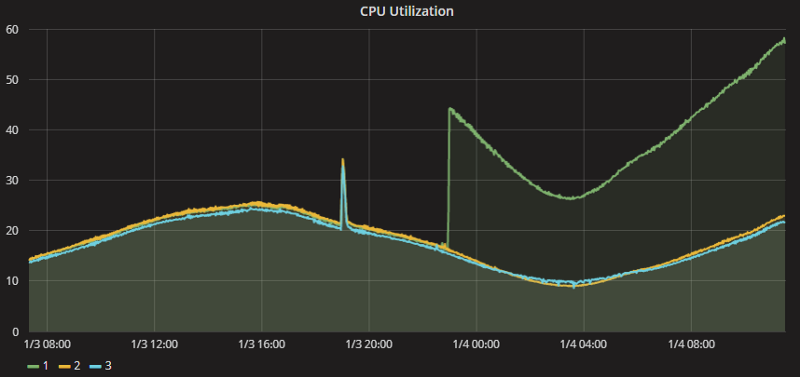
Credits : Epic Games — https://www.epicgames.com/fortnite/forums/news/announcements/132642-epic-services-stability-update
Guess, we’ll know more about general consumer level impact in coming days; but as per current data suggests there shouldn’t be any measurable impact for most day-to-day work loads.
Update - May 2019
It seems some cloud providers are facing significant losses from the patches for different vulnerabilities.
Newsletter
I strive to write low frequency, High quality content on Health, Product Development, Programming, Software Engineering, DIY, Security, Philosophy and other interests. If you would like to receive them in your email inbox then please consider subscribing to my Newsletter.