The Tallest Dwarf
Paytm says to me that it’s PoS feature didn’t have a security risk
Paytm- Alibaba backed India’s leading mobile payment wallet saw a 1000 % growth in the amount of money added to its wallet during India’s demonetisation.
I must acknowledge that digital wallets like Paytm, Ola money etc. did help in easing the pains of demonetisation for those who had access to them like me. Also we (Timebender) did our part to help people without monetising as well.
This post is not about demonetisation or its effects, this is about a particular feature rolled out by Paytm earlier last week and its security implications or more like non-acceptance of its security implications.
Earlier last week Paytm launched it’s PoS feature on its mobile apps, by which a merchant can receive payments from their customers directly.
This was a highly anticipated feature as Paytm wallet can now be used at many places to buy physical goods or services directly without it just being a payment gateway in an online portal.
 Like this cobbler. Image Source: paytm
Like this cobbler. Image Source: paytm
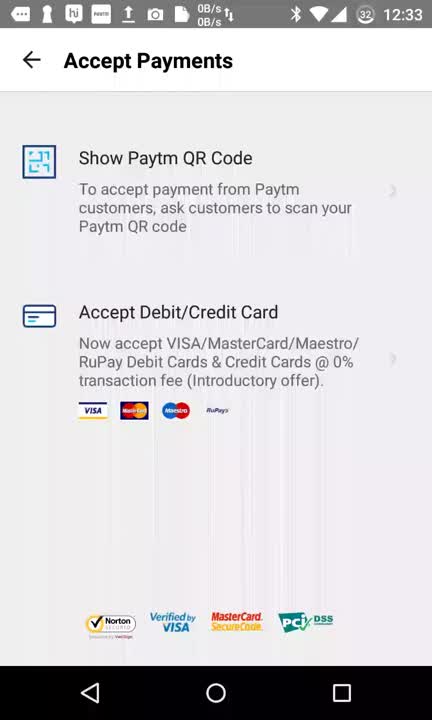
This worked by having the customers use their Paytm wallet app to pay the merchant by scanning a QR code displayed on the merchant’s Paytm app (same app).
Well it was fine till that, but Paytm went bit further to address the target population who have credit/debit cards but didn’t have Paytm wallet and that’s were things got bit too close for comfort. The customer had to type in their debit/credit card details on the merchant’s smartphone for this to work.
The customer had to type in their debit/credit card details on the merchant’s smartphone for this to work.
For an average joe, the said feature could be seen as an added convenience but for anyone who has basic understanding of security mechanisms invloved in processing card payment would see the glaring omission of security protocols to be followed.
I can summarise it to two major rules :
Rule #1 : Never ask customer to type in credit/debit card details on an untrusted device.
Rule #2 : Make sure that the merchant is not able to use your technology on a tampered device to compromise customer data.
Within hours of seeing the full front page advertisement of the said feature on a prominent national daily, we at Timebender got onto vulnerability assessment and preparation of the proof of concept for making a responsible vulnerability disclosure to the Paytm.
The POC for the security risk in the PoS feature is fairly simple, as all we needed to prove was that the merchant would be able to record the debit card/credit card details in real time using a tampered device without alerting the customer (or) altering the Paytm app.
Key logger
Though there are multiple ways the customer information could be captured in an tampered device like screen recording, screen shots, phishing Paytm app; we decided to stick with simple key logger on an android device so as to create simplest POC in which the customer cannot notice any anomaly with the device & to stick to the bounty guidelines set by Paytm.
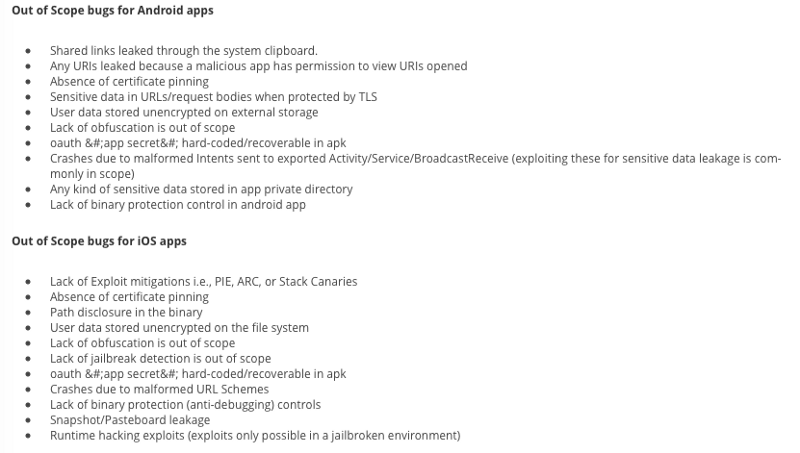 Out of scope — Paytm bug bounty guidelines
Out of scope — Paytm bug bounty guidelines
As you can see that out of scope bugs in paytm’s bug bounty guidelines are rather elaborate and it includes that jailbroken device for iOS doesn’t qualify for valid disclosure; intriguingly there are no such conditions for android’s rooted environments nor does it mention anything about keyloggers.
Web archive link for paytm bounty guidelines — here . I have included a web archive of those guidelines taken today as paytm is not sure about it’s own guidelines (shown below) and there’s acute chances of it being updated after this public disclosure.
The context of this write-up is to create awareness of the security implications to paytm and general public & so I’m going to limit in-depth technicality of the disclosure as I have added the original disclosure document to this post.
To summarise, we used a bootloader unlocked android device with xposed framework (after market modding framework) & used a simple keylogger module to record every keystrokes since it’s activated. The android device doesn’t necessarily need to be a rooted (with root privileges) device, as xposed framework can now work in a systemless environment along with magisk framework.
In this attack vector, the merchant himself uses the above said tampered device to record the card details of the unsuspecting customers in his device just to be later sold in the underground forums. This is not necessarily be the only attack vector using the key logger; the merchant themselves could fall prey to sophisticated malware based attacks which logs the keystrokes in the infected device.
Video
Video : Proof of Concept
This is a re upload of the original video, as the original video’s channel was deleted.
By watching the above video, one could understand how easy it is to record key strokes in an android device and how it could be used effectively on unsuspecting customers using pos feature of the paytm app.
Full disclosure document
Full responsible disclosure document sent to paytm.
We gave the mitigation efforts to be employed in our disclosure document.
Mitigation
Our first obivous recommendation was to avoid asking customers to enter their credit card or debit card details on an un-trusted device. Though a debit card would ask for OTP inside the India due to RBI regulations, the same debit card could be used without OTP internationally (if international payments are enabled by the particular bank).
We also suggested other mitigation mechanisms to be employed like Android’s SafetyNet API’s & iOS jailbreak detection (though official public API isn’t available, could be available to select partners like airwatch) to detect tampering of the device and prevent paytm from being used in those devices, like Android pay, Samsung pay & other international digital wallet services.
Communication with paytm
These are my email communications with paytm’s security team over the week. Due to the gravity of the situation, I mailed the disclosures myself.
24th November 2016
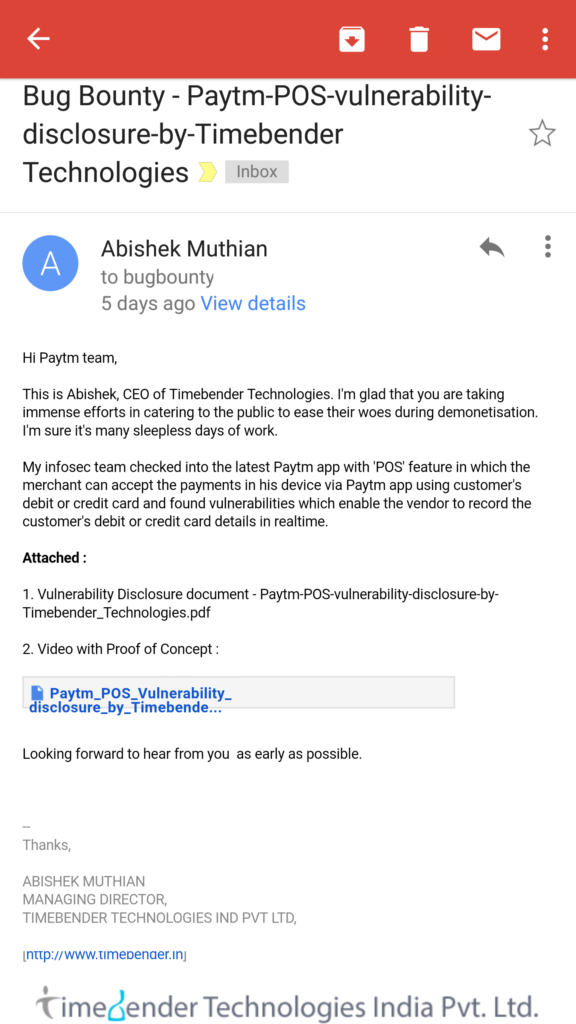 24th November 2016 (Disclosure)
24th November 2016 (Disclosure)
24th November 2016 (Reply)
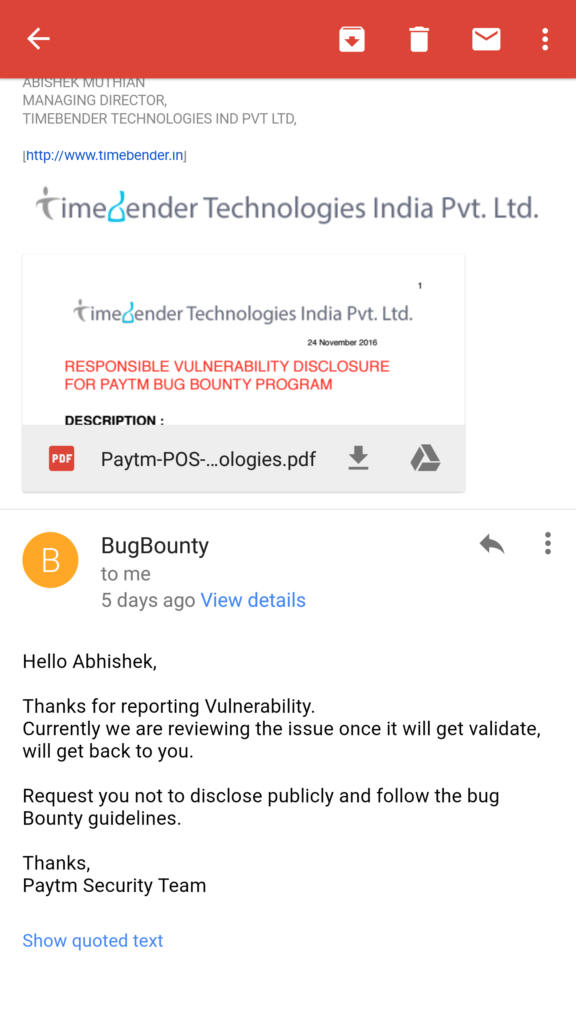 24th November 2016 (Reply)
24th November 2016 (Reply)
Received reply from the Paytm Security Team within one hour and we obliged their request to not disclose the vulnerability publicly.
25th November 2016
A day after our disclosure & I assume similar concerns raised by customers, card agencies (Visa,Mastercard) paytm removed the PoS feature to enter credit/debit card details on the merchant’s smartphone; Though it didn’t mention anything regarding security or removal of the feature in the change log of it’s mobile apps.
Media reports came out suggesting that the pressure from the card agencies regarding certification was the reason behind the roll-back of the feature. Though in all such reports, it was specifically mentioned that it’s a temporary roll-back and the PoS feature would return after adding more features.
It doesn’t end here as the communications regarding our disclosure is still pending & I wanted to know whether the roll-back was a permanent solution.
27th November 2016
BGR and other media houses quoted paytm’s CEO Vijay Shekhar Sharma saying, “You would be surprised, it is back in the App stores” !
They also quoted him saying,
Sharma replied in the affirmative when asked to confirm again if the facility is indeed live. He asserted that the security risks which the PoS offering poses are the same as the card’s use at a physical merchant where the card details can be copied.
Sharma said the company had to introduce a “few more features” before relaunching the facility, which is aimed at eliminating the need to have a swipe machine and can operate only with a mobile phone.
No Vijay, No ! The security risks which PoS offering poses are not as same as the card’s use at the physical merchant.
Here is how it differs :
- Though hacking a traditional PoS terminal (or) system isn’t that hard, it isn’t as easy as having smartphone app as the PoS either (as shown above — It took 5 mins for us to prepare the POC).
- The PoS terminal and end-to-end system needs to be certified to comply the stringent security requirements set forth by the card issuers. Who certified the smartphones, tablets, android x86 PC’s which could be used as PoS via paytm app by the merchant ?
- Why didn’t Google, Apple, Samsung decide to just throw PoS feature in their App instead of investing in NFC enabled payment terminals? (Clue : Just for this very same reason).
Note : We were not able to find the PoS feature in the latest paytm app, though we couldn’t find any media information about second roll-back, paytm informed us over mail that PoS feature is not currently in production; but was not removed due to security risk(see mail below)! Vijay didn’t know about the product team decision? Let us know if you find PoS feature being used by a merchant via paytm app.
28th November 2016
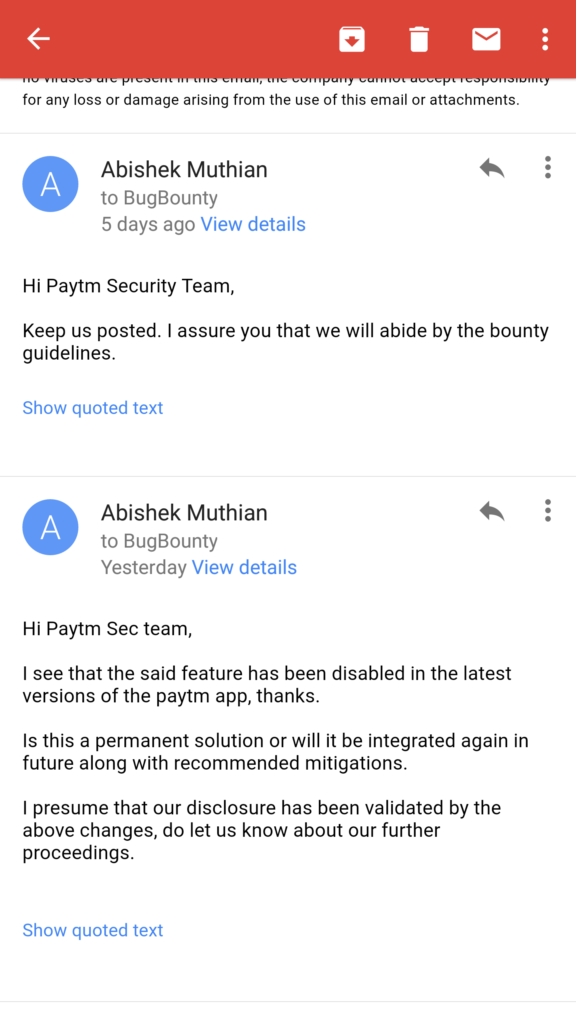 28th November 2016
28th November 2016
29th November 2016
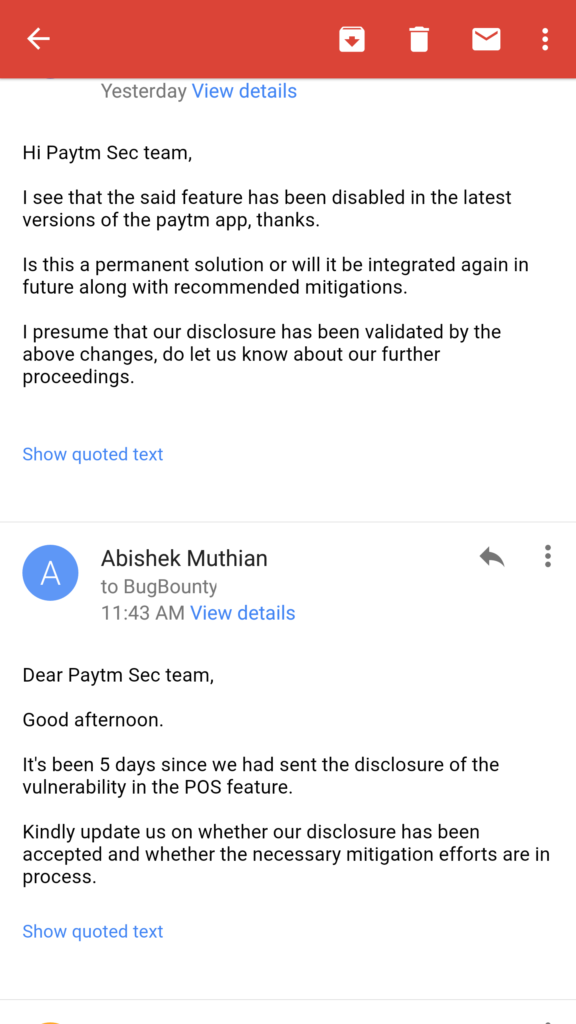 29th November 2016
29th November 2016
29th November 2016 (Paytm Reply)
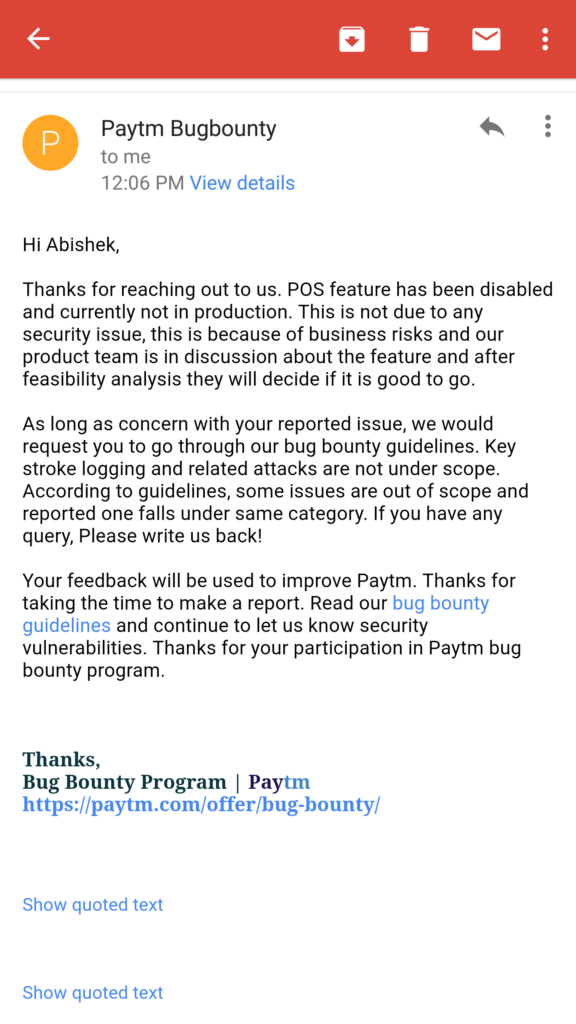 29th November 2016 (Paytm Reply)
29th November 2016 (Paytm Reply)
29th November 2016 (Final mail)
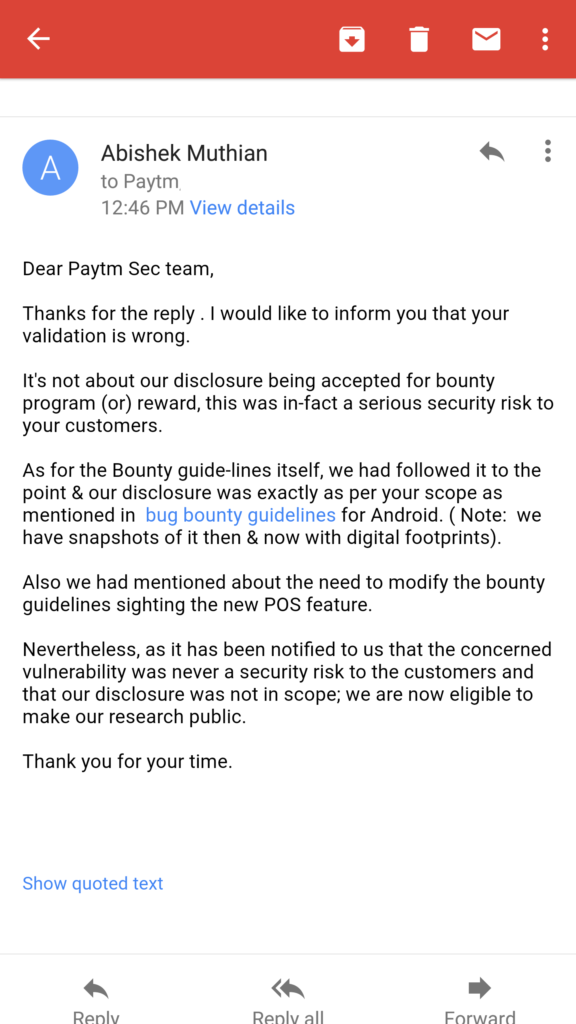 29th November 2016 (Final mail)
29th November 2016 (Final mail)
What? The only business risk paytm has is if their customers find out that their privacy and security is taken for gratend by the company holding our digital money. I’m suprised by the blatant response from the paytm security team claiming there was never a security risk & their product team will decide upon the roll-out of the said feature.
As I said to paytm, I’m least concered about their validation of the vulnerability for their reward in the bounty programme (minimum reward — 1000 INR (or) 14.5 $ with hall of fame). The reason we did make a responsible disclosure to their bounty programme is because we’re a startup which adheres to professional Information Security policies and we wanted to go by the books. Even this entire public disclosure is being done after they have rejected the disclosure as not being a security risk.
By all standards, we have made a successful disclosure according to their own guidelines. There is no mention of ‘keystroke logging’ or ‘related attacks’ in their scope of the bounty guidelines. Even if it was, it wouldn’t be valid under international standards for a PoS service via smartphone.
With over 3.2 million debit cards breached just last month, the lethargy maintained by companies whom we trust our privacy & money is unbelievable to say the least.
Especially when the government is relying on digital payment companies to ease the fallout of demonetisation for the common man by enabling technology for a digitised future; privacy & security of their products should be the top most priority.
Media coverage of this disclosure and aftermath.
Edit : The video & full disclosure document was has been added again as it was removed when the original company channel was deleted.
Newsletter
I strive to write low frequency, High quality content on Health, Product Development, Programming, Software Engineering, DIY, Security, Philosophy and other interests. If you would like to receive them in your email inbox then please consider subscribing to my Newsletter.